PSP admission controller was used by teams to validate and mutate security contexts. In simple terms, we define a set of controls with which pods can be created. If the control doesn't satisfy it rejects or updates.
PodSecurityPolicy(PSP) was deprecated in Kubernetes v1.21, and removed from Kubernetes in v1.25. What next? Instead of using PodSecurityPolicy, you can enforce similar restrictions on Pods using either or both:
Pod Security Standard (PSS)
It has 3 level of policy standard based on security contexts.
privileged — open and unrestricted
baseline — Covers known privilege escalations while minimizing restrictions
restricted — Highly restricted, hardening against known and unknown privilege escalations. May cause compatibility issues
Detail regarding each policy- https://kubernetes.io/docs/concepts/security/pod-security-standards/
Pod Security Admission (PSA)
It perform actions based on the PSS policy. Policies are applied in a specific mode. Multiple modes (with different policy levels) can be set on the same namespace. Here is a list of modes:
enforce — Any Pods that violate the policy will be rejected
audit — Violations will be recorded as an annotation in the audit logs, but don't affect whether the pod is allowed.
warn — Violations will send a warning message back to the user, but don't affect whether the pod is allowed.
Let's See in action-
pod-security.kubernetes.io/<MODE>= <LEVEL>
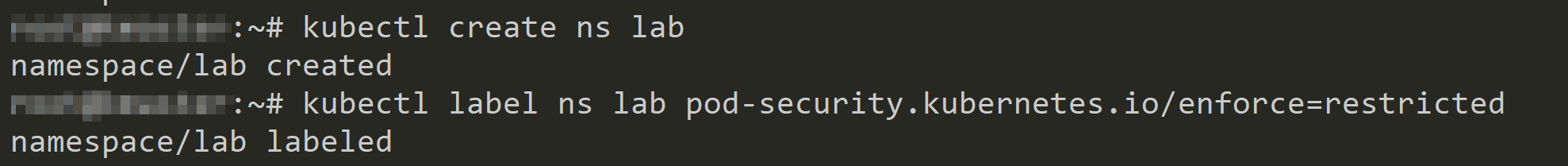
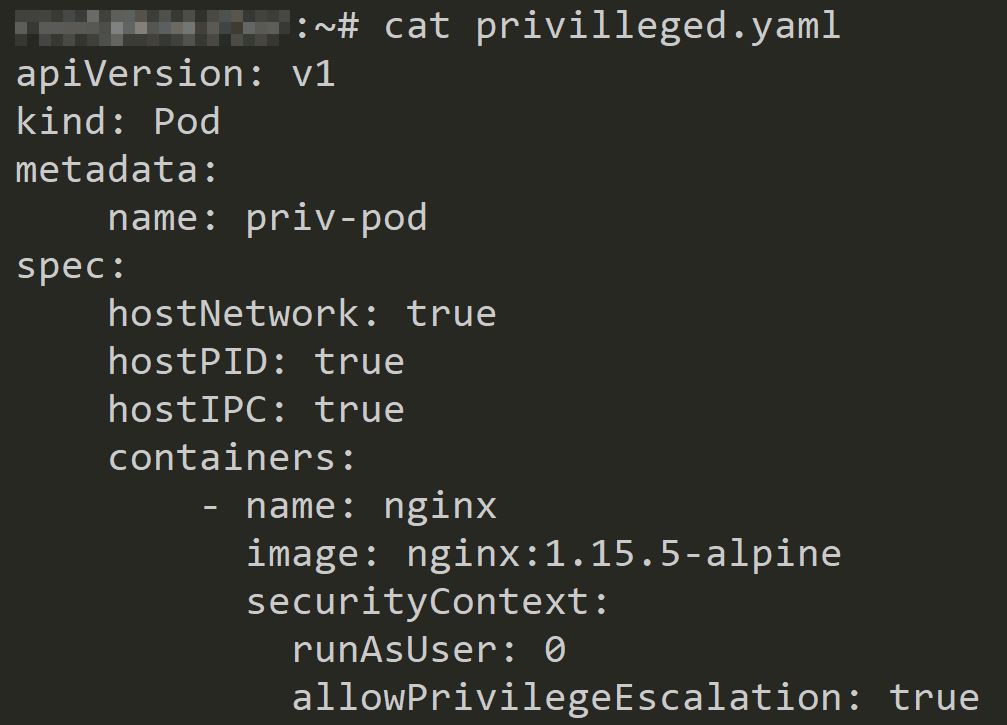
Create a privileged pod and apply the policy
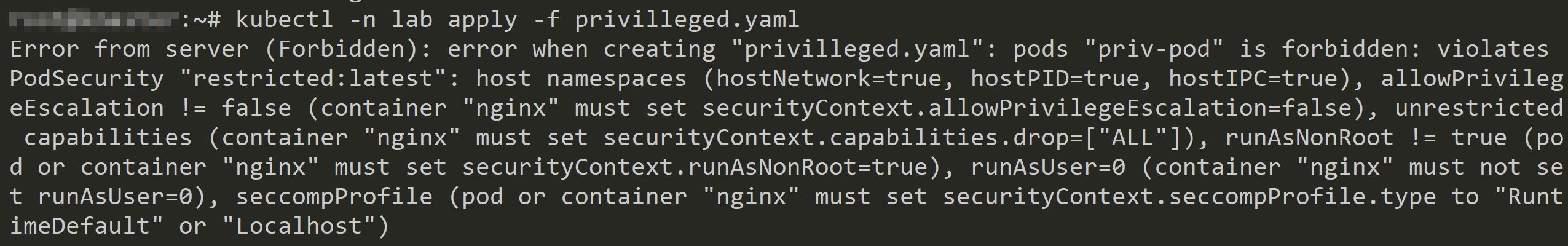
As you can see pod was rejected due to policy violations.
Additional Info-
- If you want cluster-wide configuration with exemptions, but that requires modifying static manifest file --admission-control-config-file.
- Modifying admission controller files can halt your kube-apiserver operation for a few minutes. That's why I would personally recommend PSA with kyverno for admission controller.
- Note if you are applying via yaml files- For v1.23 and v1.24, use v1beta1. For v1.22, use v1alpha1. For v1.25+ pod-security.admission.config.k8s.io/v1 .
- Almost all managed clusters like GKE have PSA available for cluster versions above 1.23.
- You can modify existing policy by just overwriting labels.
kubectl label --overwrite ns psp \
pod-security.kubernetes.io/enforce=restricted \
pod-security.kubernetes.io/audit=restricted