
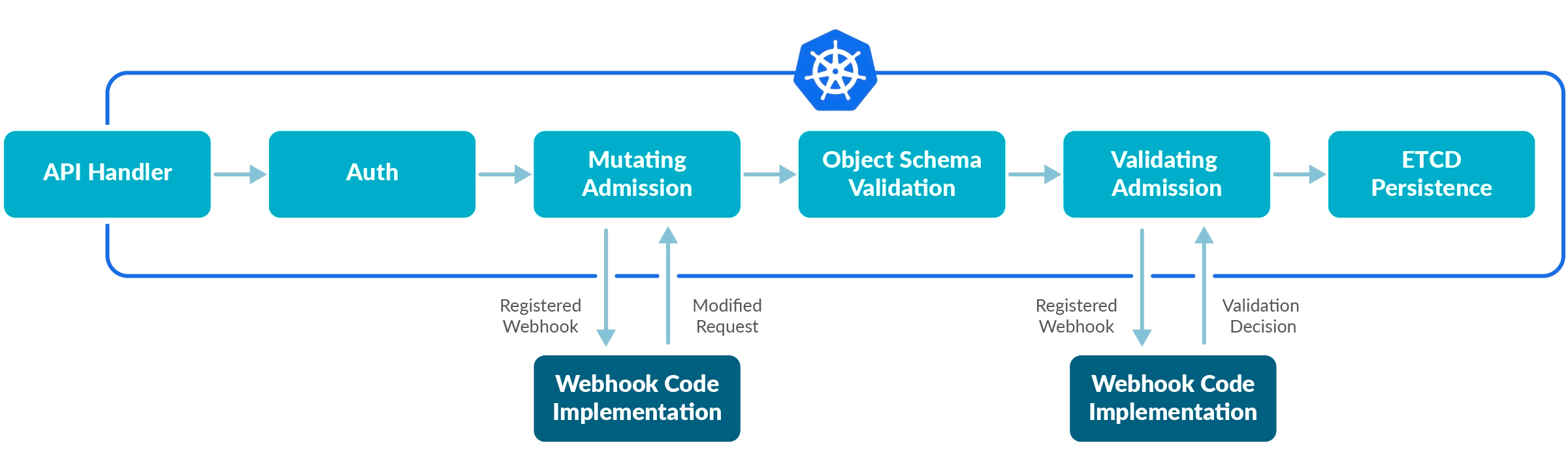
- Limit requests to create, delete, modify, and other specific operations
- Allows enforcing granular rules
- Highly effective in hardening Kubernetes clusters
A new ServiceAccount called 'default' is created whenever a new Namespace is created. Pods spawned in that Namespace, by default will be mounting this ServiceAccountToken. With this service token, you can communicate with kube-Apiserver.

According to security best practices it is recommended to disable mounting the ServiceAccountToken. There are 2 ways to do it. By attaching automountServiceAccountToken: false to the ServiceAccount itself or in the POD spec itself. Configure service account for pods.
Kyverno policy to implement disable service account token mount- here. Now due to the mutation-based webhook whenever a new namespace is created, it will automatically add automountServiceAccountToken: false.
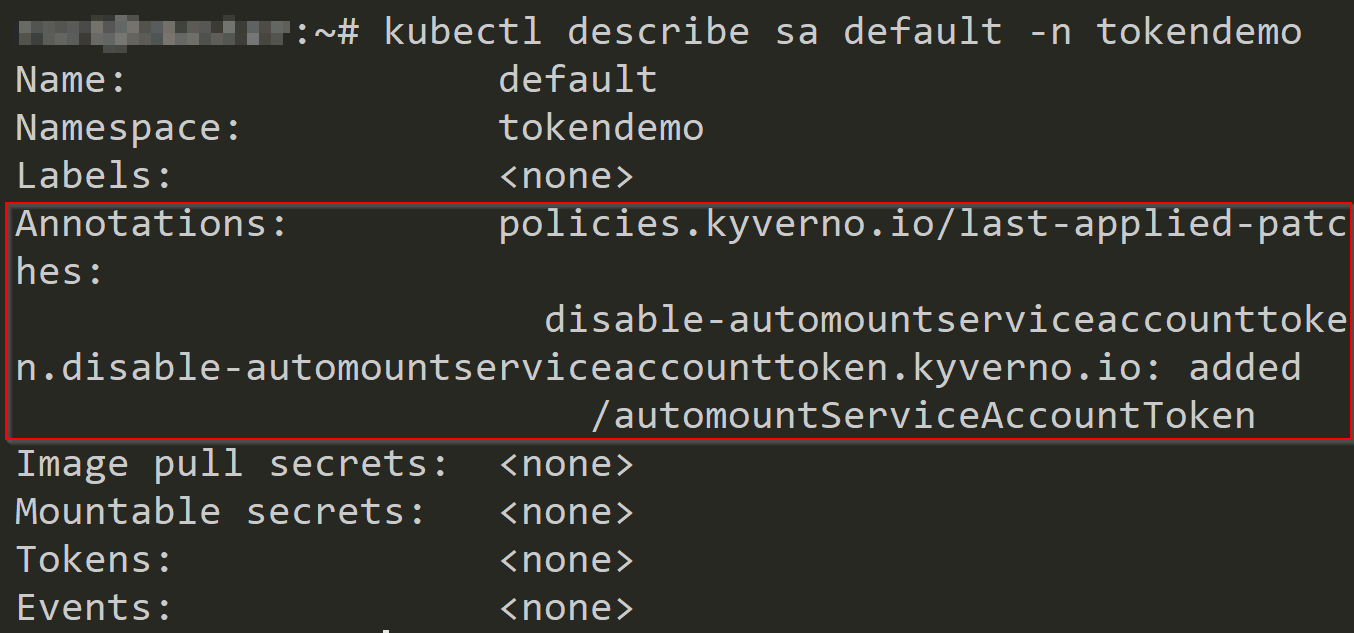
Now tokens are not mounted automatically.
2. Only allow images to be pulled from the organization registry
Allowing images from other or public registry introduce the risk of having a backdoor image in Kubernetes infra. Usually, organization registry images are scanned periodically & most org have golden images. So we will use a policy that denies images from other registries than the org registry. policy. As of now, the policy is configured in audit mode which will only show a warning. You can put in "enforce" mode to completely block, but before doing that make sure all the images including master component images are in your org registry.


As you can see it is showing error “ validation error : Unknown Image registry”.
3. Mutate the registry to our private registry.
"Security engineering should be a business enabler not a blocker for different teams". Let's create a policy if anyone mistakenly pulls images from the public registry, mutating webhook automatically changes to our private registry. policy.
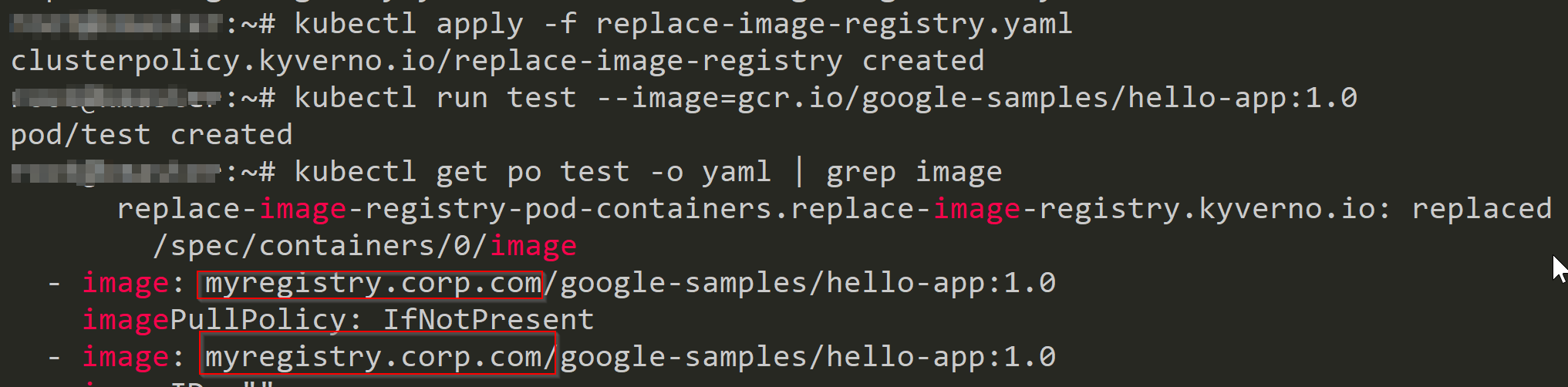
Magic !! you can see the registry automatically changed to myregistry.corp.com .








