In simple terms with Azure policy, you can audit, deny, and modify if any resource is misconfigured. It's very helpful for creating secure defaults in Azure Cloud.
why would you create secure defaults?
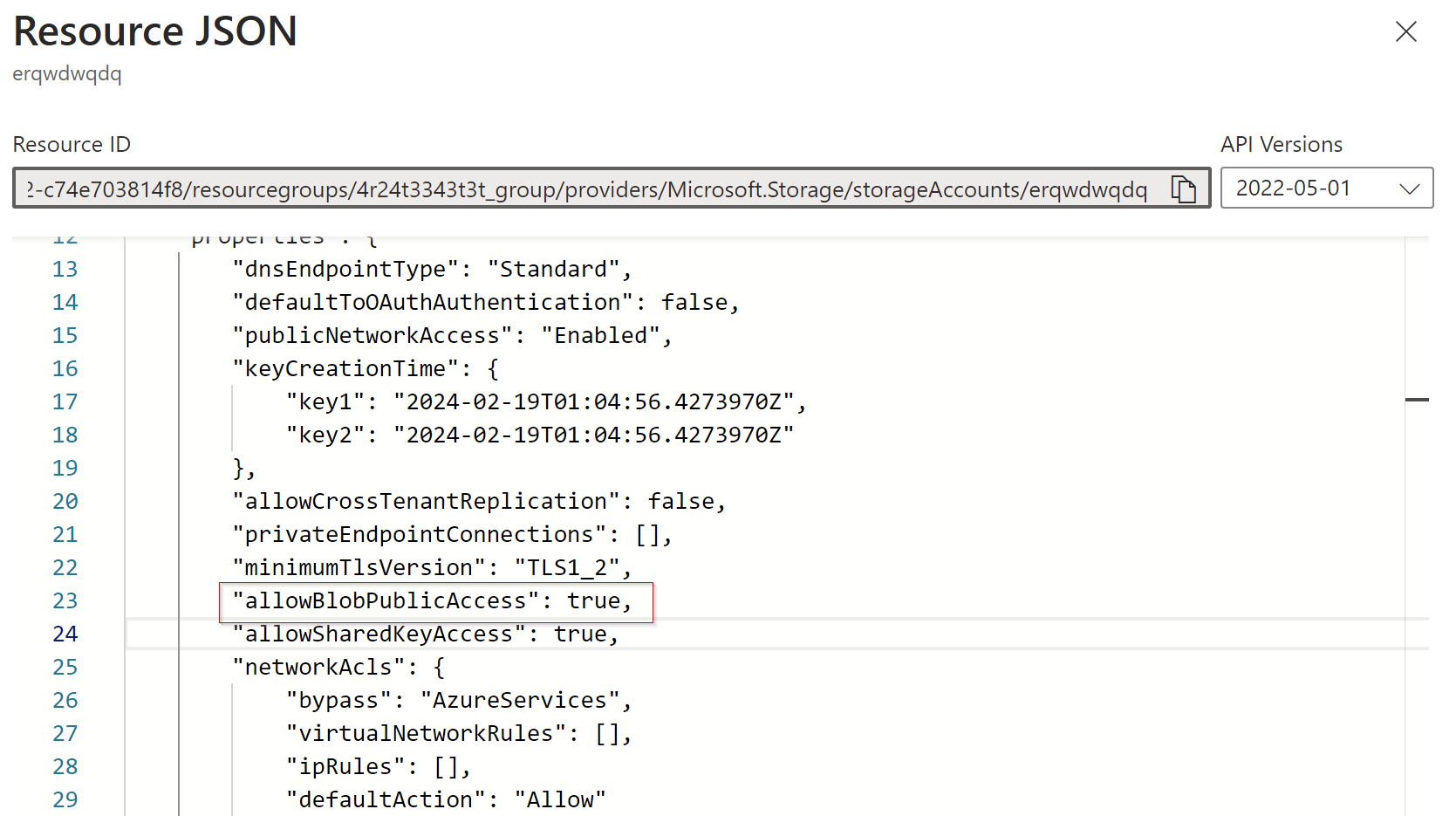
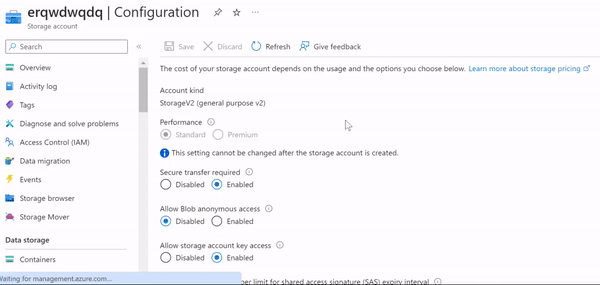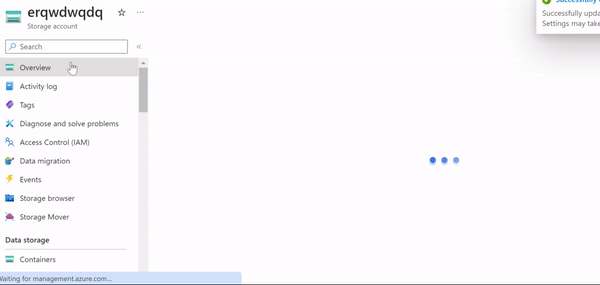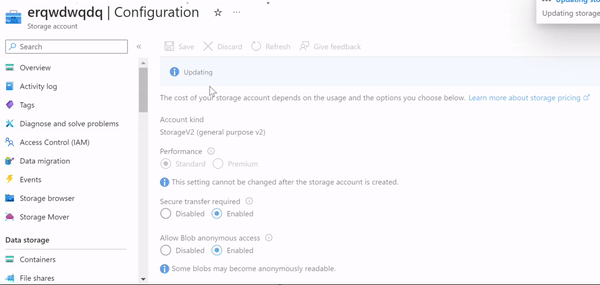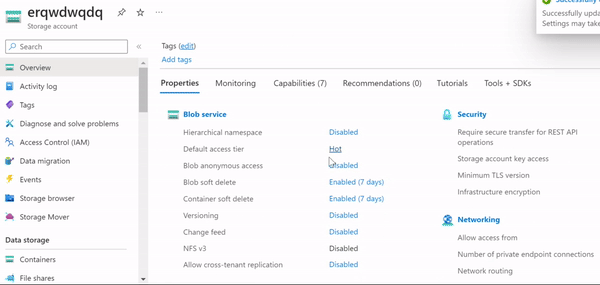
For example, if someone from your organization is creating a blob storage, he may allow anonymous access. If you find a storage account public during the scan, then you might consider your data is already breached.
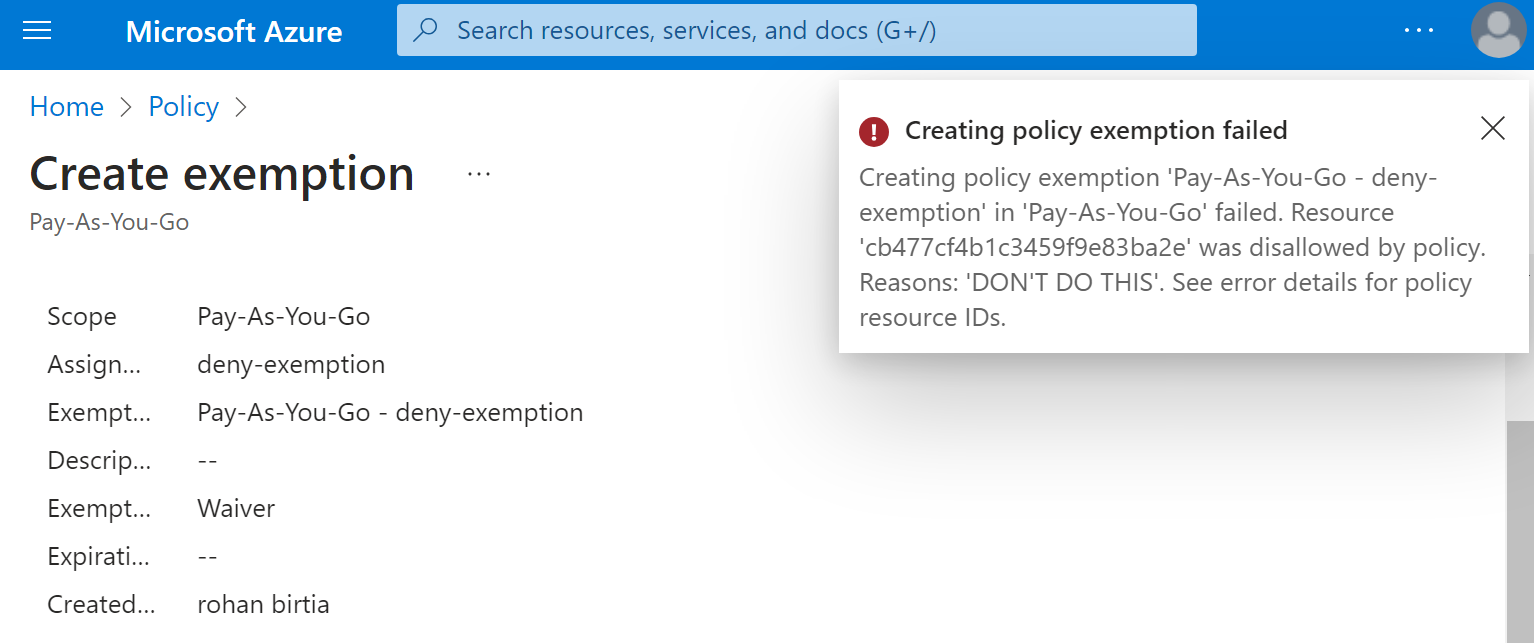
Also let's say you fixed certain cloud misconfigurations, after a month again these misconfigurations pop up & You will end up in non-compliance.
Basic of Azure Policy -
- In policy definition, you can specify a conditional match based on the available resource API value and set actions according to the conditions. A set or group of policies can be combined into an initiative, which makes it easier to manage and enforce broader governance objectives. Applying policies through initiatives provides a more comprehensive approach to governance.
- There are 2 types of policy. Built-in and custom.
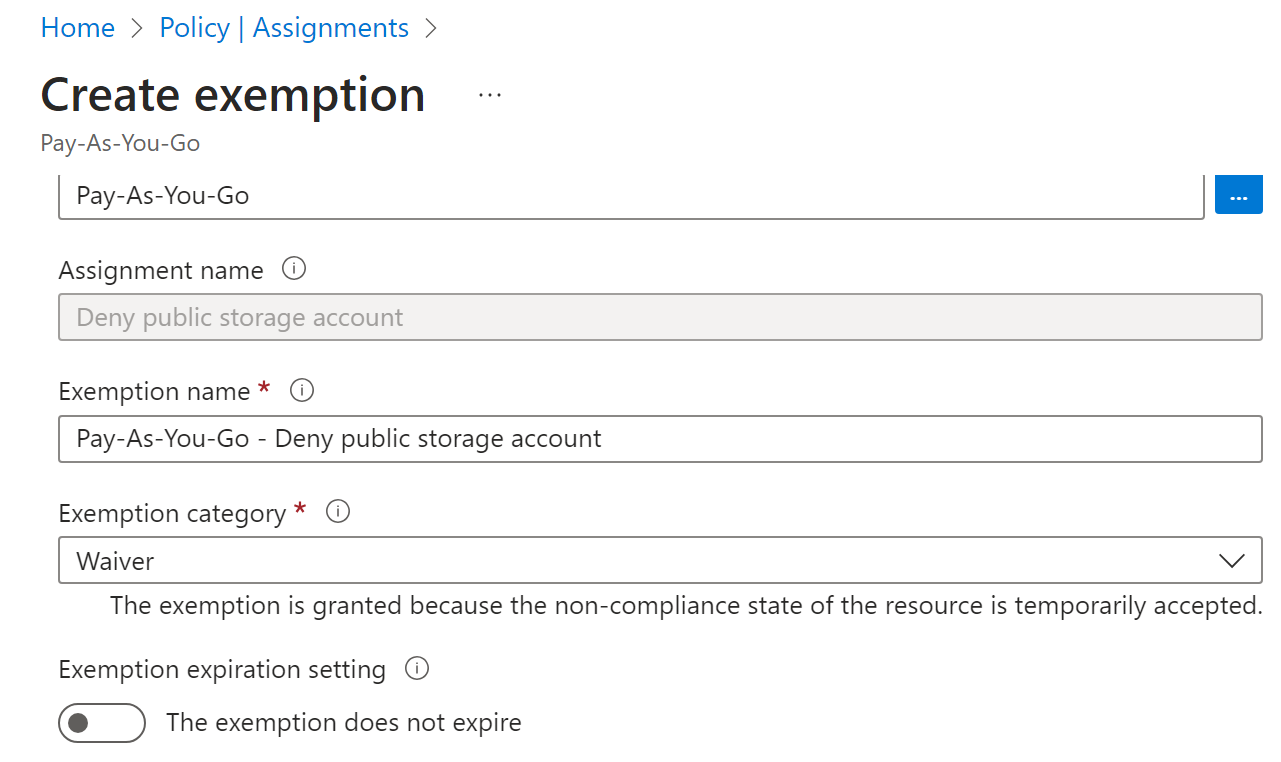
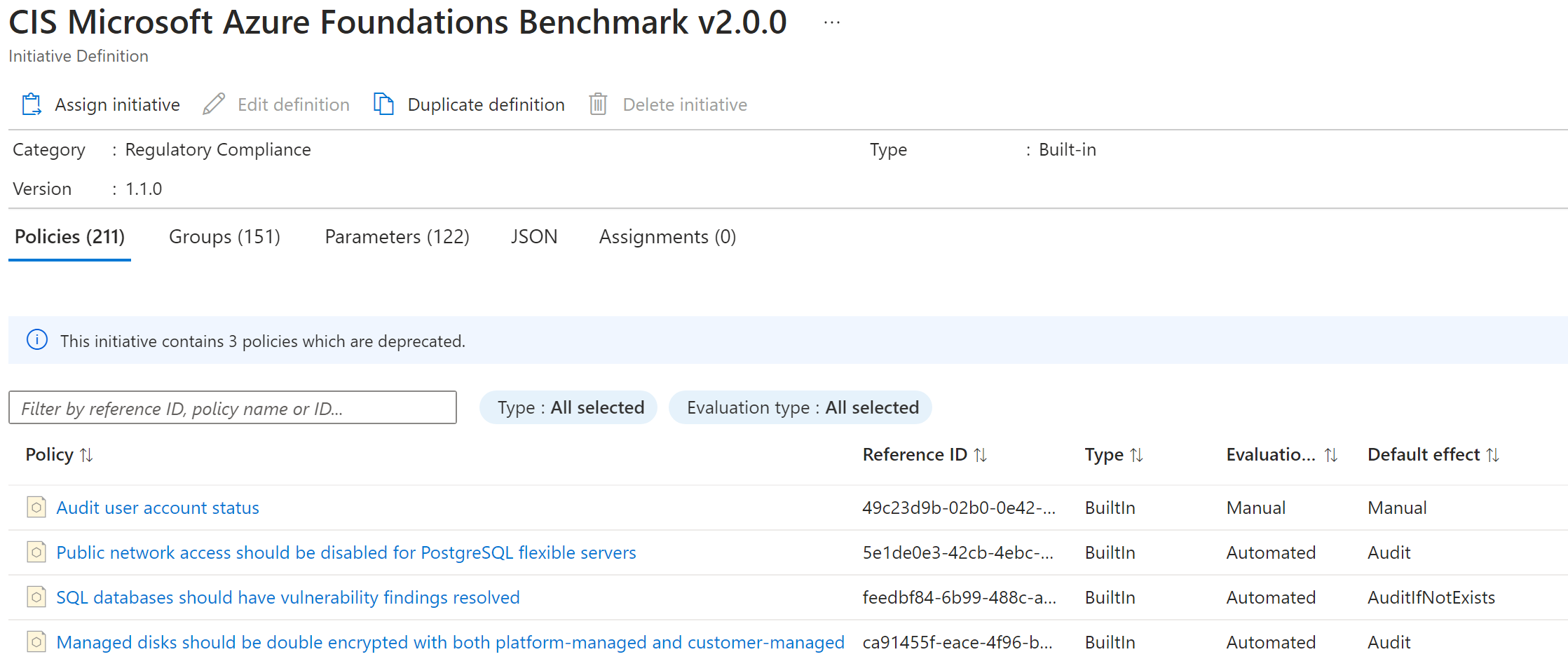
- There are a lot of built-in policies for example above the CIS benchmark initiative. But note the effect, all of them are on audit. That's why we will create a custom policy to control the action and set exceptions according to our wishes.
- There are 2 types of modes in policy (All, Indexed). Index mode only evaluates resource types that support tags and location. Azure recommends using the "All" mode. https://learn.microsoft.com/en-us/azure/governance/policy/concepts/definition-structure#resource-manager-modes.
- Also, note that multiple effects of policies can be applied to the same resource. Please follow the order of evaluation- https://learn.microsoft.com/en-us/azure/governance/policy/concepts/effects#order-of-evaluation
- Azure policy doesn't modify existing resources, but in case of any state change, it will check the API values. This helps onboarding policies without breaking your infrastructure unlike GCP policies, where policies applied will affect existing resources also.